
How Security Teams Can Resolve Incidents Faster and Better with Security Orchestration
May 22, 2019
Taking Things to the Next Level with Security Automation
May 28, 2019A Match Made in Technology
Heaven: When Machine Meets Human
Imagine a security operations team where your analysts are not overwhelmed with alerts, are able to find and stop new threats within minutes and feel highly motivated in their jobs.
It’s an ideal security operations team, isn’t it?
Although, it’s true that technology may never completely substitute humans, at the same time it’s becoming progressively more clear that automation can offer a distinct value to your security operations beyond what any living, breathing employee could. Here’s why.
Your incident response team, the guys handling security threats to protect your organization around the clock, might be really good at monitoring alerts, creating tickets or making decisions but they can never compete with the response time and efficiency of an automation tool.
Time is a threat actor’s ally – and a SOC team’s enemy
A significant number of the day-to-day processes in a SOC are repetitive and can take a redundant amount of time when done manually. Pair this with a consistently developing inundation of alerts and a lack of accessible security resource, and there, you have a recipe for security operations filled with risks.
According to a study conducted by EMA, 67% of organizations were only able to investigate 10 or fewer of their severe/critical events per day 88% of the participants indicated their teams were only able to investigate 25 or fewer severe/critical events per day.
What can happen? Well, there is a chance that 60% of some of these unresolved alerts or events can jeopardize your whole business causing some serious implications.
According to Verizon’s 2018 Data Breach Investigations Report, there have been more than 2,200 data breaches in 2018. About 90% of these data breaches were executed in a minute or less, yet virtually all of them took months or longer to discover.
Similarly, the biggest security breach in Facebook's history took the company 4 days to discover and 11 more days to stop it.
In many cases, it’s not even the organization itself that spots the breach—it’s often a third party, like law enforcement or a partner. Worst of all, many breaches are spotted by customers and we all know how bad that would be for an organization’s reputation.
Between the growing number of alerts and the number of tools needed to detect them, whether your security team has two people, ten people or you can double that number, it has become nearly impossible for security teams to manually address each alert thoroughly and to keep up with non-stop cybersecurity attacks.
Of course, it sounds disappointing.
Well, where do we go from here? This is where the Security Orchestration, Automation and Response (SOAR) solution comes into play.
Drastically Reduce Response Time
A solution that doesn’t need to take a coffee break, doesn’t get distracted as it works 24/7 and doesn’t sleep so you can proactively hunt down each threat as it occurs. It also eliminates the chances of an error made by a tired and overworked analyst. While, it takes about 25 minutes or more of an analyst’s efforts for the manual process per security incident, spend a few seconds to respond to a security incident through Automation and Orchestration.
Greater Visibility
Best of all, SOAR integrates smoothly with your existing security technologies for two-way interactions that track alerts and manage the process for fast response time, maximum uptime and minimum risk. The more you aggregate and collaborate all the necessary incident information into a single console, you can free up your team’s attention and allocate it to where you need it the most without any disturbances.
Combine the expertise and intuition of skilled security analysts with the power of machine learning automation
As complex as it may sound, this collaborative effort can level up your security game by providing maximum efficiency while saving time and money in the process. How?
Let’s take a look at how automation works:
A user interacts with a malicious IP address.
A user tries to access a particular website and the IP address of that website is detected as suspicious. An alert will be escalated via SIEM to SOAR which will lookup URL reputation in several databases of malicious sites and against threat intelligence feeds for the domain and IP address. If any malicious indicators are found, it will trigger a process to identify the details of the affected user from Active Directory. Based on those results, SOAR will perform decision making that whether the endpoint needs to be contained or that malicious website needs to be blocked on the web gateway.
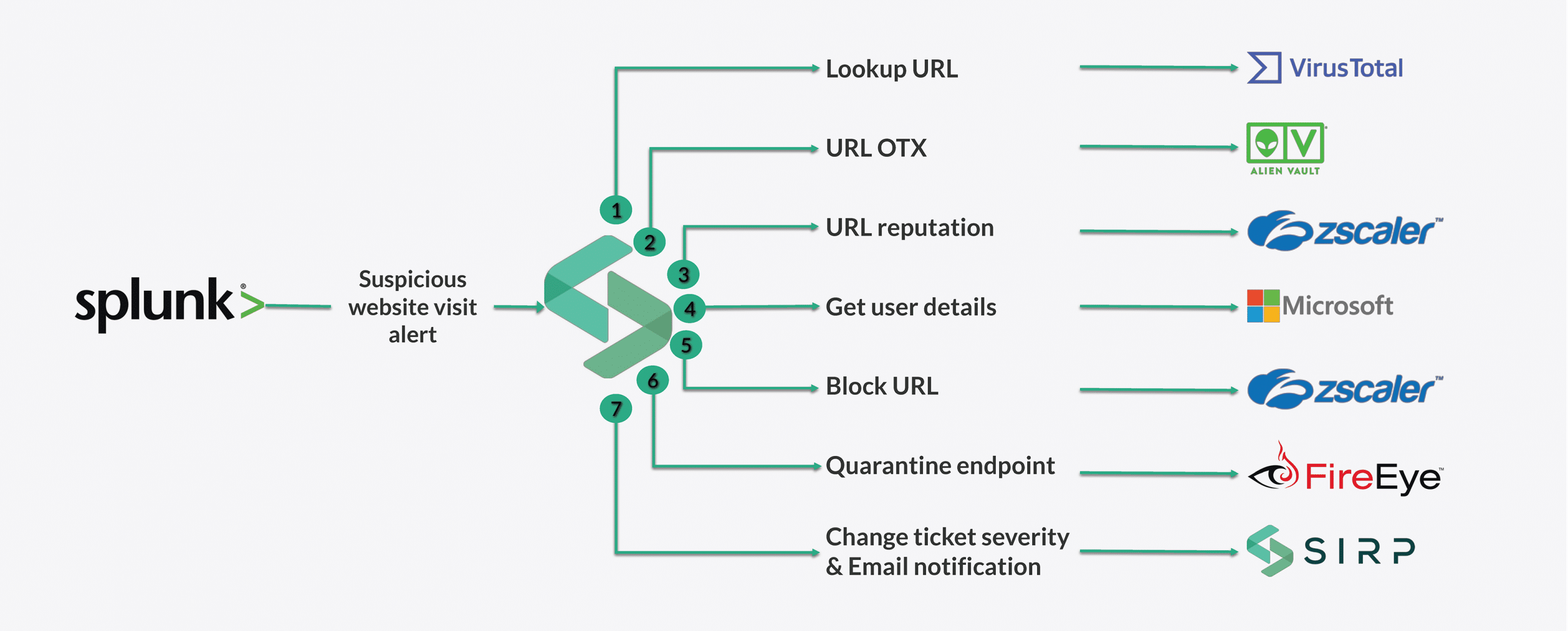
98% Reduction in Response Time
As this real example illustrates, If a human had manually performed this elongated process, it would have taken him more than an hour, whereas with automation it took less than 2 minutes. The result? Response times are 10 times faster, missed breaches are dramatically reduced and analysts are much happier!
Let’s analysts realize their full potential
Security Automation enables security operations teams to realize their full potential and work more cohesively and consistently while combating cyberthreats. It greatly improves the efficiency and effectiveness of security operations and frees up analyst’s time for more valuable tasks.
With all the best practices and hours of every lesson learned, the platform continues to implement the appropriate course of action, investigating the same way an analyst would but at machine speed in order to resolve every issue and protect your most critical data, whether or not you are awake to trigger the action.
To keep up with the pace of cybersecurity alerts. According to Gartner, “By 2019, 40% of organizations will entail specialized, automated tools to meet regulatory requirements in the event of a serious information security incident.”
No viable threat is too small to investigate
The incident response needs to be dynamic and swift. Why? Because there is an adaptive, malicious adversary on the other end. You need a response system that does not let any alert go vague; consequently letting some threats slip through the cracks.
It’s time to act.
It is time to make a change in the right direction. If any of these signs ring a bell, it may be time for your organization to invest in security automation and experience for yourself what an incredible transformation automated incident management truly can make for your organization.
