Autonomous SOC
From Playbooks to Decision Systems
Security operations were built for human-paced threats. Modern attacks operate at machine speed. The SOC operating model must evolve.
An Autonomous SOC is a security operations model where AI systems independently analyze alerts, compute risk, decide response actions, and execute remediation within defined governance boundaries. Unlike traditional SOAR platforms that automate static workflows, an Autonomous SOC enables decision-driven security operations.
Autonomous SOC
From Playbooks to Decision Systems
Autonomous SOC
From Playbooks to Decision Systems
Security operations were built for human-paced threats. Modern attacks operate at machine speed. The SOC operating model must evolve.
An Autonomous SOC is a security operations model where AI systems independently analyze alerts, compute risk, decide response actions, and execute remediation within defined governance boundaries. Unlike traditional SOAR platforms that automate static workflows, an Autonomous SOC enables decision-driven security operations.
The SOC Was Not Designed for This World
The SOC Was Not Designed for This World
Security Operations Centers were designed around assumptions that no longer hold.
They assumed alerts were manageable.
They assumed humans could correlate signals in real time.
They assumed scale meant adding people.
Those assumptions quietly collapsed.
Modern incidents are not single alerts. They are multi-stage attack chains spanning email, identity, endpoints, cloud workloads, and user behavior — unfolding faster than humans can reliably reason about in sequence.
This is not a failure of analysts.
It is a failure of the operating model.
Security Operations Centers were designed around assumptions that no longer hold.
They assumed alerts were manageable.
They assumed humans could correlate signals in real time.
They assumed scale meant adding people.
Those assumptions quietly collapsed.
Modern incidents are not single alerts. They are multi-stage attack chains spanning email, identity, endpoints, cloud workloads, and user behavior — unfolding faster than humans can reliably reason about in sequence.
This is not a failure of analysts.
It is a failure of the operating model.
Why Automation and SOAR Reached a Ceiling
Why Automation and SOAR Reached a Ceiling
Automation was a necessary step — but it was never the destination.
SOAR accelerated execution. It did not change how decisions were made.
Playbooks encode predefined paths for known conditions. Attackers do not follow predefined paths. As environments became more dynamic and attacks more adaptive, static automation became brittle.
The result was predictable:
Endless tuning
Growing exception lists
Human overrides everywhere
Automation without reasoning simply moves the bottleneck downstream.
Automation was a necessary step — but it was never the destination.
SOAR accelerated execution. It did not change how decisions were made.
Playbooks encode predefined paths for known conditions. Attackers do not follow predefined paths. As environments became more dynamic and attacks more adaptive, static automation became brittle.
The result was predictable:
Endless tuning
Growing exception lists
Human overrides everywhere
Automation without reasoning simply moves the bottleneck downstream.
Why the Industry Is Rebuilding — Not Optimizing
Why the Industry Is Rebuilding — Not Optimizing
The current wave of cybersecurity consolidation is often described as optimization.
That framing misses the deeper shift underway.
Strategic buyers are no longer prioritizing incremental detection, additional controls, or workflow expansion. They are responding to a more fundamental realization: the security operating layer itself no longer scales.
The industry is not optimizing the SOC.
It is rebuilding it around decision systems.
The current wave of cybersecurity consolidation is often described as optimization.
That framing misses the deeper shift underway.
Strategic buyers are no longer prioritizing incremental detection, additional controls, or workflow expansion. They are responding to a more fundamental realization: the security operating layer itself no longer scales.
The industry is not optimizing the SOC.
It is rebuilding it around decision systems.
From Alert Handling to Decision Systems
From Alert Handling to Decision Systems
Legacy security platforms are optimized for handling alerts.
Modern security requires systems optimized for making decisions.
Alert-centric architectures assume humans will correlate context, prioritize risk, and decide when to act. That assumption no longer holds at machine scale.
Decision-centric architectures operate differently:
Context is assembled automatically
Risk is evaluated continuously
Actions are proposed or executed within policy
Humans are involved only where judgment adds value
This is not about removing humans.
It is about removing them from being the bottleneck.
Legacy security platforms are optimized for handling alerts.
Modern security requires systems optimized for making decisions.
Alert-centric architectures assume humans will correlate context, prioritize risk, and decide when to act. That assumption no longer holds at machine scale.
Decision-centric architectures operate differently:
Context is assembled automatically
Risk is evaluated continuously
Actions are proposed or executed within policy
Humans are involved only where judgment adds value
This is not about removing humans.
It is about removing them from being the bottleneck.
Autonomy With Governance
Autonomy With Governance
Autonomy does not mean loss of control.
Human-driven SOCs already operate with uncontrolled variance — different analysts make different decisions, fatigue changes outcomes, and escalation paths are inconsistent.
AI-native autonomy, when designed correctly, is more governable, not less.
Effective autonomous security systems operate within:
Explicit policies
Risk-tiered approval gates
Blast-radius constraints
Full auditability and reversibility
Autonomy is not binary.
It is deliberately bounded.
Autonomy does not mean loss of control.
Human-driven SOCs already operate with uncontrolled variance — different analysts make different decisions, fatigue changes outcomes, and escalation paths are inconsistent.
AI-native autonomy, when designed correctly, is more governable, not less.
Effective autonomous security systems operate within:
Explicit policies
Risk-tiered approval gates
Blast-radius constraints
Full auditability and reversibility
Autonomy is not binary.
It is deliberately bounded.
The Economics Force the Shift
The Economics Force the Shift
Human-centric SOCs scale linearly.
Threats scale exponentially.
As alert volume increases, analyst fatigue rises, response times slow, and error rates grow. Costs increase predictably while outcomes remain inconsistent.
AI-native decision systems change the economics:
Alerts become inputs, not work
Spikes become learning events, not stress events
Marginal cost per alert approaches zero
Outcomes become more predictable over time
This is not just cheaper security.
It is sustainable security.
Human-centric SOCs scale linearly.
Threats scale exponentially.
As alert volume increases, analyst fatigue rises, response times slow, and error rates grow. Costs increase predictably while outcomes remain inconsistent.
AI-native decision systems change the economics:
Alerts become inputs, not work
Spikes become learning events, not stress events
Marginal cost per alert approaches zero
Outcomes become more predictable over time
This is not just cheaper security.
It is sustainable security.
The Real Risk Has Changed
The Real Risk Has Changed
Historically, the risk for CISOs was moving too early.
Today, the greater risk is standing still.
Boards are no longer satisfied with dashboards, alert counts, or tool inventories. They care about decision speed, adaptability, and outcome consistency.
The question is no longer whether AI will change security operations — but whether leaders adapt their operating model in time.
Historically, the risk for CISOs was moving too early.
Today, the greater risk is standing still.
Boards are no longer satisfied with dashboards, alert counts, or tool inventories. They care about decision speed, adaptability, and outcome consistency.
The question is no longer whether AI will change security operations — but whether leaders adapt their operating model in time.
Humans Are Repositioned — Not Removed
Humans Are Repositioned — Not Removed
AI-native security does not remove human responsibility.
It refocuses it.
Humans remain essential for:
Defining policy and acceptable risk
Governing autonomy boundaries
Handling business-critical decisions
Auditing outcomes and accountability
The future SOC is human-on-the-loop, not human-in-the-loop.
AI-native security does not remove human responsibility.
It refocuses it.
Humans remain essential for:
Defining policy and acceptable risk
Governing autonomy boundaries
Handling business-critical decisions
Auditing outcomes and accountability
The future SOC is human-on-the-loop, not human-in-the-loop.
Go Deeper
For a detailed technical explanation — including architecture, decision flows, governance boundaries, and learning loops — read the founder-authored whitepaper:
This page is the canonical guide to SIRP’s Autonomous Security narrative. It is intended for architectural and strategic understanding, not product marketing.
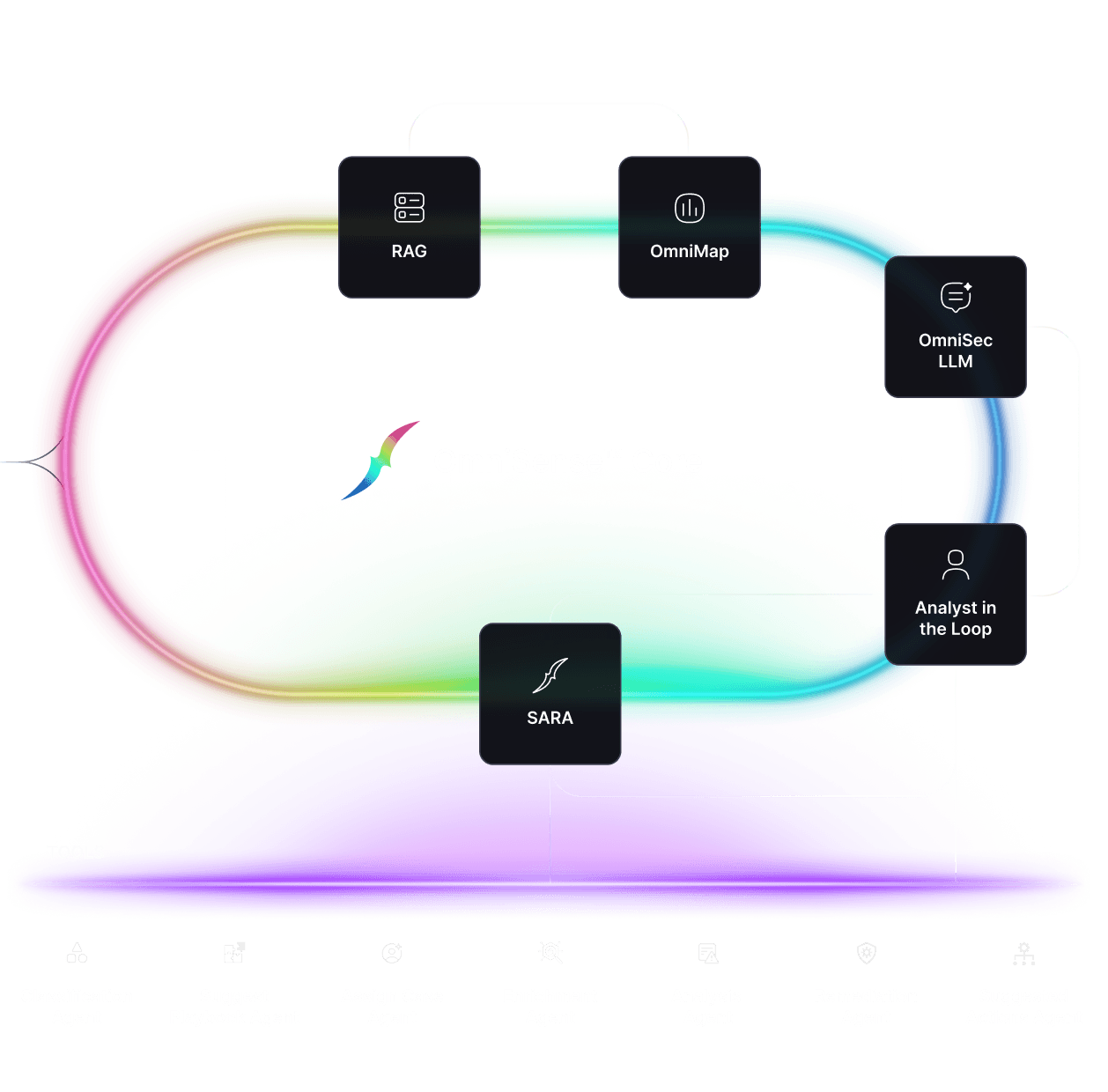
Watch your Autonomous SOC drive itself
Watch your Autonomous SOC drive itself
Watch your Autonomous SOC drive itself
This page is the canonical guide to SIRP’s Autonomous Security narrative. It is intended for architectural and strategic understanding, not product marketing.
United States
7735 Old Georgetown Rd, Suite 510
Bethesda, MD 20814
+1 888 701 9252
United Kingdom
167-169 Great Portland Street,
5th Floor, London, W1W 5PF
© 2026 SIRP Labs Inc. All Rights Reserved.
United States
7735 Old Georgetown Rd, Suite 510
Bethesda, MD 20814
+1 888 701 9252
United Kingdom
167-169 Great Portland Street,
5th Floor, London, W1W 5PF
© 2026 SIRP Labs Inc. All Rights Reserved.
United States
7735 Old Georgetown Rd,
Suite 510, Bethesda, MD 20814
+1 888 701 9252
United Kingdom
167-169 Great Portland Street,
5th Floor, London, W1W 5PF


© 2026 SIRP Labs Inc. All Rights Reserved.